
Security experts at Scam Sniffer have warned of a new tactic where attackers steal cryptocurrencies by faking a “transaction simulation.” In just one incident, hackers stole 143.45 ETH (approximately $460,000) within 30 seconds.
1/8 🚨 SECURITY ALERT: A victim lost 143.45 ETH ($460,895) through transaction simulation spoofing 1 day ago.
— Scam Sniffer | Web3 Anti-Scam (@realScamSniffer) January 10, 2025
Here's how these attacks work… 🧵 pic.twitter.com/IQTSS8I3dp
Some Web3 wallets offer a feature that lets users preview a transaction’s outcome before signing. This is meant to increase transparency, allowing them to verify the amount being transferred, fees, and other details on the blockchain.
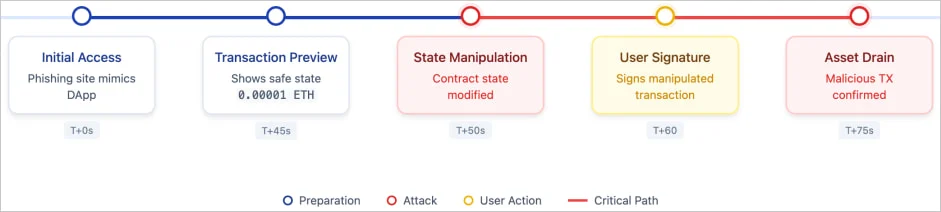
The scammers exploit a vulnerability in this preview mechanism. They lure victims to a malicious site promising a small amount of Ethereum. The user can then see a preview of the “claim” transaction.
4/8 💻 The attack sequence:
— Scam Sniffer | Web3 Anti-Scam (@realScamSniffer) January 10, 2025
• Phishing site initiates a "Claim" ETH transfer
• Wallet simulates tiny ETH receipt (0.000…0001 ETH)
• Backend modifies contract state
• Actual transaction drains wallet pic.twitter.com/0iNmQOLL5E
However, the time delay between the simulation and the actual execution gives attackers an opportunity to change the contract’s state on-chain. If the user signs the transaction, the hackers can drain their wallet.
Developer Recommendations Scam Sniffer experts suggest that Web3 wallet developers adjust the frequency of transaction simulation updates to align with the actual block creation time. They also advise forcing a fresh simulation result before critical operations, alerting users to the heightened risk.
Context
- In late 2024, Scam Sniffer exposed a similar fraudulent scheme using fake influencers and malicious Telegram bots to steal crypto assets.








 Cryptol – your source for the latest news on cryptocurrencies, information technology, and decentralized solutions. Stay informed about the latest trends in the digital world.
Cryptol – your source for the latest news on cryptocurrencies, information technology, and decentralized solutions. Stay informed about the latest trends in the digital world.