
North Korean hackers are organizing fake calls to cryptocurrency project founders from supposed venture investors on the Zoom platform to steal confidential data.
Having audio issues on your Zoom call? That's not a VC, it's North Korean hackers.
— Nick Bax.eth (@bax1337) March 11, 2025
Fortunately, this founder realized what was going on.
The call starts with a few "VCs" on the call. They send messages in the chat saying they can't hear your audio, or suggesting there's an… pic.twitter.com/ZnW8Mtof4F
According to Nick Bax from Security Alliance, this method has allowed scammers to steal “tens of millions of dollars.”
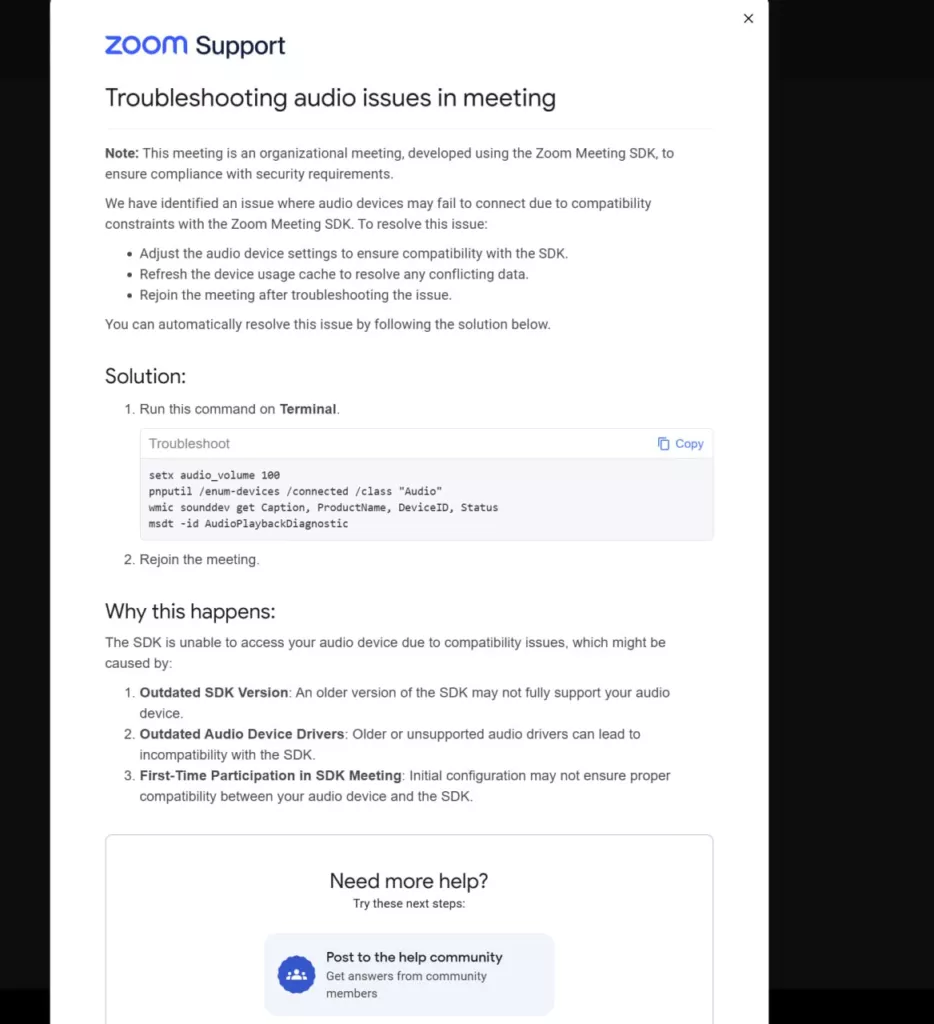
The scammers initiate contact with offers of funding or partnerships. Once the call begins, text chat messages appear about sound issues, and the victim typically sees a “venture investor” waiting to talk.
The scammers then provide a link to a different Zoom conference, suggesting a patch to fix the issue.
“They exploit human psychology — you think you’re meeting important venture capitalists and rush to fix the sound, which makes you less cautious than usual. Once you install the file, you’re done,” explained the expert.
Upon realizing the mistake, Bax advises immediately disconnecting the device from the internet, turning it off, and contacting specialists.
Julio Ksilyannis, co-founder of the gaming Web3 protocol Mon Protocol, confirmed that scammers attempted to deceive him and the head of marketing. The hackers disguised the contact as the CEO of Story Protocol, who immediately mentioned sound issues.
Ksilyannis was asked to follow a new Zoom link and suggested running the fix.
“When I saw partners from Gumicryptos and Superstate talking, I knew something was wrong,” said the entrepreneur.
David Zhang, co-founder and CTO of Stably, commented on a similar situation:
“Another day, another North Korean scammer.”
Another day another North Korean scammer
— David Zhang (▲) (@dazhengzhang) March 12, 2025
This time using the same "fake Zoom" scam that's been popular recently
I'll detail what happened to me in this 🧵 pic.twitter.com/X5UZAKJjR0
He took the call on his tablet, and the scam tools, including the “fake Zoom,” seemed not to be adapted for mobile operating systems. As a result, the scammers got confused and ended the call.
Zhang admitted that he was unsure how it would have ended if he were on his computer.
Melvin Thomas, the founder of Devdock AI, admitted that he may have been affected by the hackers’ actions.
The same thing happened to me. But didnt give my password while the install was happening.
— Melbin (melbin.eth) (@melbint04) March 12, 2025
Disconnecte my laptop and I reset to factory settings. But transferred my files to a hard drive. I have not connected the hard drive back to my laptop. Is it still infected? @_SEAL_Org
“The same thing happened to me. But I didn’t give my password while the installation was happening,” he wrote in response to Bax’s post.
Thomas turned off his laptop and reset it to factory settings. He immediately transferred his files to an external hard drive, but he wasn’t fully confident that the virus hadn’t been activated.
It’s worth noting that hackers from the North Korean Lazarus Group have launched a new attack vector targeting cryptocurrencies through the GitHub platform for developers.








 Cryptol – your source for the latest news on cryptocurrencies, information technology, and decentralized solutions. Stay informed about the latest trends in the digital world.
Cryptol – your source for the latest news on cryptocurrencies, information technology, and decentralized solutions. Stay informed about the latest trends in the digital world.