
После серии арестов и деанонимизации администраторов даркнет-платформ пользователи Tor Browser начали задаваться вопросами о безопасности этого инструмента. Ведущие эксперты, связанные с его разработкой, попытались прояснить ситуацию.
Основной волной беспокойства стало раскрытие киберпреступников властями Германии, которые смогли деанонимизировать участников даркнета с использованием временного анализа трафика. Среди выявленных — владельцы и активный пользователь крупнейшего даркнет-сайта Boystown, занимающегося незаконной деятельностью.
Временной анализ не связан с уязвимостями в программном обеспечении, но через длительный мониторинг трафика позволяет определить личность пользователя.
Команда Tor призналась, что не знает точно, как именно власти Германии достигли деанонимизации, но предположила, что была использована уязвимость в устаревшем мессенджере Ricochet, которым пользовался один из задержанных.
«Помимо улучшений пропускной способности и добавления ретрансляторов, команда Tor недавно внедрила новые функции для усиления защиты, повышения скорости и производительности», — заявил Павел Зонефф, директор по стратегическим коммуникациям Tor в интервью Cointelegraph.
Однако, по словам Михала Поспишальски, генерального директора компании MatterFi, атаки с использованием временного анализа всегда остаются возможными.
Лазейка в системе безопасности
В опубликованном расследовании Panorama отмечается, что метод, использованный для атаки, был нацелен на «охранные ноды» или серверы входа, которые используются для связи через Ricochet.
«Мы полагаем, что атака на пользователя старой версии Ricochet была связана с уязвимостью через атаку на охранные узлы», — пояснил Зонефф.
Когда трафик проходит через Tor, он направляется через три набора узлов — входные, промежуточные и выходные. В случае сервисов, таких как Ricochet, выходной узел отсутствует, а трафик не выходит за пределы сети Tor, что затрудняет его отслеживание. Но, как предполагают эксперты, правоохранители могли захватить несколько промежуточных узлов, что повысило вероятность успешного анализа трафика.

«Это типичная атака Сивиллы», — отметил Ор Вайнбергер, генеральный директор компании Brute Brother, добавив, что для ее реализации необходимы значительные ресурсы.
Устаревший метод и улучшения
Хотя описанные атаки вызвали волну беспокойства, с момента инцидента прошло уже три года, и команда Tor значительно улучшила систему безопасности. В частности, Ricochet был обновлен до новой версии Ricochet-Refresh с механизмом защиты Vanguard, что делает подобные атаки сложнее.
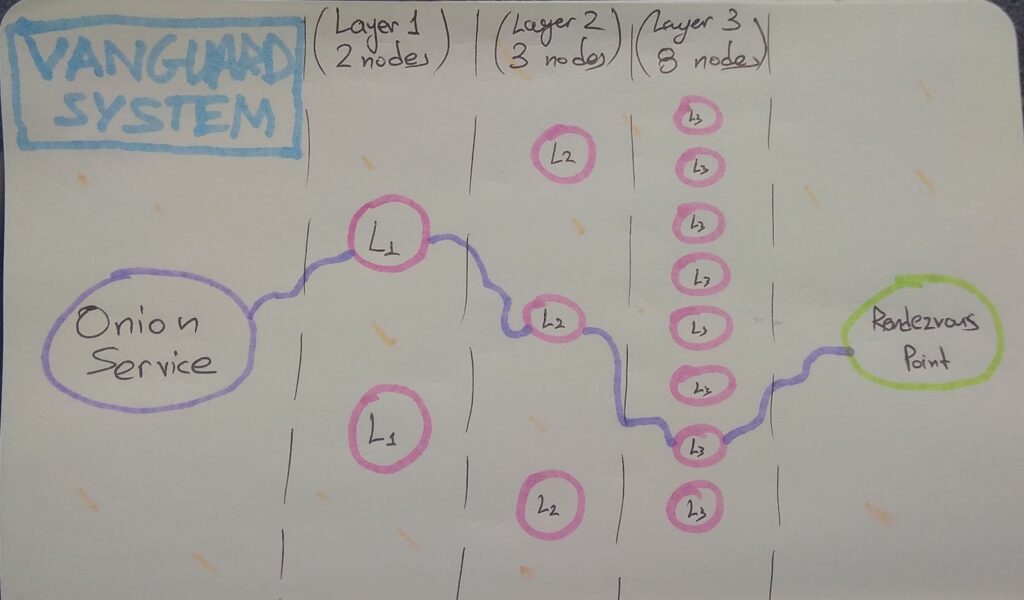
«Любая система безопасности всегда может быть подвергнута атаке, но разработчики оперативно устраняют обнаруженные уязвимости», — отметила Лиза Лауд, исполнительный директор Secret Foundation.
Доминирующая роль Германии
Сегодня большая часть ретрансляторов сети Tor расположена в Германии, что вызывает дополнительные вопросы о потенциальной возможности отслеживания трафика. Согласно последним данным, в стране находятся 1852 из 8085 ретрансляторов.
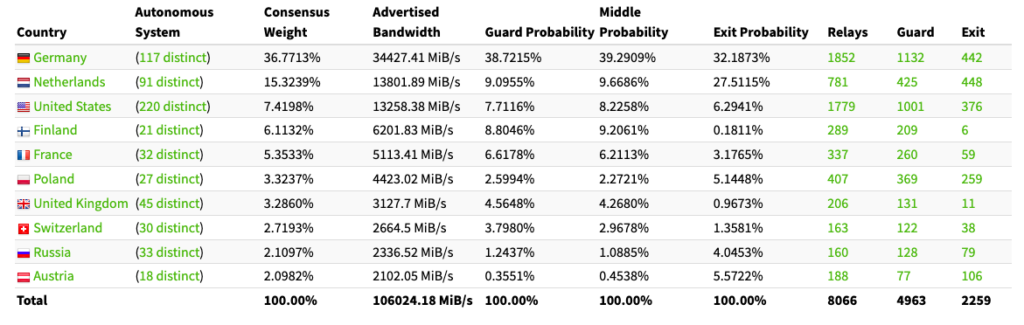
«Ваш клиент Tor с большей вероятностью выберет высокопроизводительный охранный узел, что делает атаки более вероятными со стороны государств», — пояснил Вайнбергер.
Большинство экспертов считают, что для обычных пользователей Tor по-прежнему остается безопасным, но преступникам стоит быть начеку.
«Анонимность в интернете может быть сохранена, но все зависит от того, как будут развиваться технологии», — подытожила Лауд.
Напомним, что летом 2023 года ряд операторов программ-вымогателей начали перемещать свою деятельность из даркнета в Telegram.








 Cryptol — новости о криптовалютах, информационных технологиях и децентрализованных решениях. Оставайтесь в курсе актуальных событий в мире цифровых технологий.
Cryptol — новости о криптовалютах, информационных технологиях и децентрализованных решениях. Оставайтесь в курсе актуальных событий в мире цифровых технологий.